Espionage Under the Cover of Organizations: How Sana’a Foiled the American–Israeli–Saudi Joint Operations Project
On a morning that began like any other news day, quiet voices from within Yemen rose to reveal a complex, cross-border intelligence web. The Ministry of Interior made an announcement, withholding details pending investigation and analysis—until the full, unsettling truth emerged: a special security operation had uncovered a spy network linked to a joint operations room established by foreign intelligence services, headquartered in Saudi Arabia.
What makes this revelation remarkable is not merely the arrest of agents or the containment of a sabotage effort, but the scale of foreign involvement, the internal recruitment mechanisms, the professional sophistication of the network, and the exposure of activities that directly affected Yemen’s civilian, military, and economic fabric.
This report narrates the uncovering and investigation as an analytical story—how the network was formed, how it operated, how civilian fronts were exploited as covers, and what the suspects’ confessions revealed about the enemy’s strategies for striking Yemen from within.
Birth of the Joint Operations Room and Engineering the Network
The story begins where the adversaries least wish light to fall—behind shaded offices and maps spread across side tables, encrypted communications, and unseen officers orchestrating from behind screens.
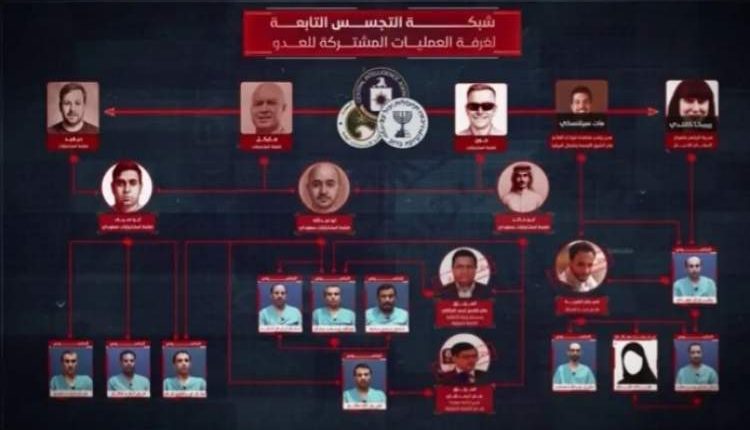
The joint operations room that united American, Israeli (Mossad), and Saudi intelligence was not born by chance; it was conceived as a response to what they viewed as past failures and a need to change their tools of attack. Instead of direct confrontation, they chose infiltration: a web of small, compartmentalized cells, each with a specific task, operating in silence until impact.
The structure was methodical—a central command issuing directives and providing tools, while local cells worked intermittently to minimize the risk that one exposed cell could compromise others.
These cells were not only assigned targets but trained in precision reporting, coordinate gathering, and the use of encrypted communication apps, miniature cameras, and advanced devices to relay information to handlers abroad.
The Human Story: From Recruitment to Betrayal
Perhaps the most striking aspect of this story is its human dimension, reflected in the suspects’ confessions—where personal hardship meets manipulation and betrayal.
Each individual detained had a different entry point: one was recruited through a humanitarian organization, another lured by a promised job or small salary, and a third by the hope of escaping unemployment.
What united them was not ideology, but calculated exploitation of social and economic vulnerability. Recruitment often began with local intermediaries who knew precisely where to start—meetings in hotels or public centers, promises of financial support, and the handing over of seemingly civilian assignments to deflect suspicion.
Those drawn in underwent technical training—how to operate equipment, write coded reports, conceal and transmit data. Humanitarian or civil-society organizations were used as fronts to facilitate meetings and movement.
Behind every “project” or “aid initiative” was a covert operational channel designed to feed information outward.
Espionage Tools and Concealment Tactics
The tools seized exposed alarming levels of sophistication: advanced devices, encrypted communication software, and high-precision location tools capable of turning any site into a potential target.
This was not improvisation but the result of funding and deliberate planning.
Camouflage was essential to the espionage ecosystem: humanitarian projects projecting legitimacy, fake companies offering “jobs” or “surveys,” casual meetings in public places, and the veneer of financial exchange that made espionage look like ordinary work.
Such tactics reveal that modern warfare no longer confines itself to battlefields—it extends into the heart of civil life.
Direct Threats and Consequences
The suspects’ statements went beyond the technical—they exposed intent: mapping missile launch points, storage sites, leadership locations, and public infrastructure, from power stations to hospitals, as well as reporting on shipping routes and supply lines.
Such information, in hostile hands, could have turned into targeted strikes designed to inflict maximum civilian and infrastructural damage.
Even more dangerous, the network’s role extended beyond military spying; it reportedly contributed to economic sabotage by feeding intelligence on supply chains and essential facilities, aiming to weaken Yemen’s resilience from within.
Thus, espionage became part of a broader campaign—not just to undermine the military, but to erode the nation’s social and moral core.
State and Society: The Role of Vigilance
The operation’s success also stands as proof of local